Enhancing Software Supply Chain Security
Tools for dependency analysis, vulnerability assessment and supply chain security files generation. Secure your software supply chain with advanced dependency exploration and VEX document generation.
Our Security Tools
Three powerful open-source tools designed to work together for comprehensive supply chain security
Constructs full dependency graphs from package manifests (npm, pip, Maven, etc.) and detects vulnerable transitive dependencies. Visualizes them in Neo4j for exhaustive analysis.
Key Features
- • Multi-language package support
- • Transitive dependency detection
- • Neo4j graph visualization
- • Vulnerability scanning
Automated tool that generates VEX (Vulnerability Exploitability eXchange) documents indicating exploitability status for software artifacts, integrating with OSV and SBOMs.
Key Features
- • Automated VEX generation
- • OSV database integration
- • SBOM compatibility
- • Exploitability assessment
Secure Chain MCP Server enables AI assistants and LLMs to interact directly with our security tools through the Model Context Protocol, providing seamless integration for AI-powered security analysis.
Key Features
- • MCP protocol integration
- • AI assistant compatibility
- • Real-time security queries
- • LLM-powered analysis
Secure Chain Data Dumps
This repository contains files and scripts to initialize and populate Secure Chain's databases. It includes information on ~270,000 vulnerabilities and ~260,000 exploits. The second database holds a dependency graph with ~4.4M packages and ~64.6M versions from NPM, PyPI, Ruby Gems, Cargo Crates, and partially Maven.
View Data DumpHow They Work Together
Depex and VEXGen complement each other to provide complete software supply chain security
Understanding the Secure Chain Workflow

This diagram illustrates the integrated workflow of Depex and VEXGen within Secure Chain. Requirement files (like SBOM, pom, txt) are fed into Secure Chain. Depex handles graph building, visualization, vulnerability attribution, and solver reasoning, leading to outputs like graphs, vulnerabilities, and dependency configurations. VEXGen performs static code analysis, integrates intelligence threat information, and generates VEX documents. This combined approach ensures a complete security analysis of your software supply chain.
Use Cases
Real-world applications for enhanced supply chain security
Large organizations can audit their entire software portfolio for vulnerabilities and maintain compliance documentation.
Integrate into your development pipeline for automated vulnerability scanning and VEX document generation on every build.
Maintainers can provide transparency about their project's security posture and dependency health to users.
System Architecture
An overview of Secure Chain's robust and scalable microservices architecture.
Secure Chain's Integrated Architecture
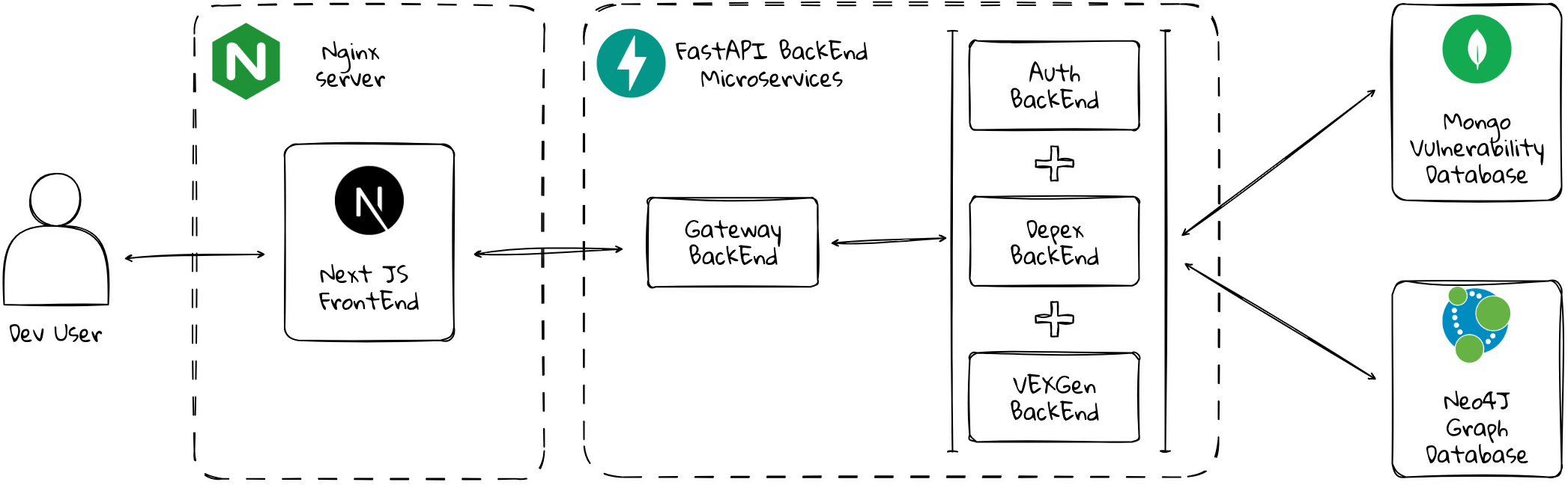
The Secure Chain architecture is designed for scalability and efficiency. A Developer User interacts with the Next.js FrontEnd, which is served statically by Nginx, and which communicates with a Gateway BackEnd. This gateway routes requests to various FastAPI BackEnd Microservices, including Auth BackEnd for authentication, Depex BackEnd for dependency analysis, and VEXGen BackEnd for VEX document generation. These microservices leverage a Mongo Vulnerability Database for vulnerability data and a Neo4j Graph Database for dependency graph storage, ensuring comprehensive and performant security analysis.
Get in Touch
Have questions, feedback, or want to collaborate? Reach out to us!
Get in touch with us:
[email protected]Our Supporters
Secure Chain is proudly supported by leading research institutions committed to advancing cybersecurity

IDEA Research Group
University of Seville
Leading research in software engineering, data analysis, and intelligent systems with a focus on innovative solutions for complex technological challenges.
Visit IDEA
I3US Institute
Institute of Computer Engineering, University of Seville
Dedicated to advancing research and innovation, fostering collaboration between academia and industry in the development of cutting-edge technology.
Visit I3USThese institutions provide invaluable support through research collaboration, academic expertise, and commitment to open-source cybersecurity advancement.